JILT 2002 (1) - Caroline Allinson
Audit Trails in Evidence - A Queensland Case Study
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
|
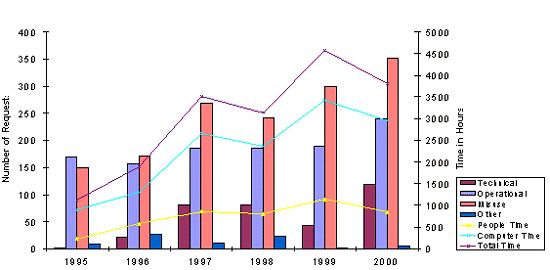
Figure 1: Audit Trail Investigation Requests with Time
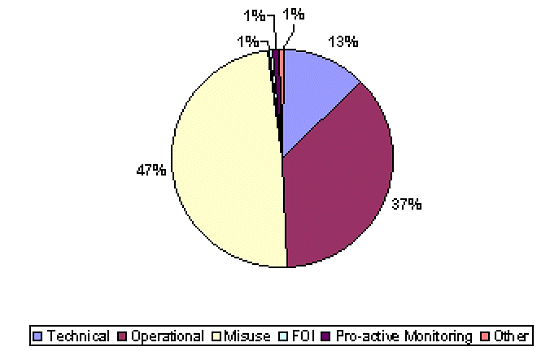
For the six year period 1995 to 2000, three thousand and two (3,002) requests for audit trail searches were received. This equates to approximately 1.37 requests per day based on a 365 day year. Of these received requests 13 percent were technical, 37 percent were operational, 47 percent were misuse, 1 percent were other, 1 percent were pro-active monitoring of systems use and 1 percent were FOI (Figure 2).
|
|
Figure 2: Six Year Percentage For Requests
Requests for Audit Trail investigation are accepted from a QPS Commissioned Officer or equivalent Manager. There are many and varied ways in which the data can be searched. A request may involve:
-
a time frame, i.e; all activity between January 15, 1999 through December 12, 1999;
-
a persons name, i.e. who has queried 'Joe Bloggs';
-
a vehicle number or vehicle numbers, i.e. who has queried vehicle number 'AAA 111';
-
all activity in relation to a user, i.e; what activity was performed by user '1234567';
-
all activity in relation to a transaction, i.e; who used transaction 'TRAN123';
-
all activity in relation to a terminal or location, i.e. who performed activity from terminal 'TERM123'.
Results may be used as intelligence information in a police investigation or may be incorporated into the 'record of interview' when a suspect or accused person is being questioned in relation to an offence. Many are required in evidence and the security officers from ISS, who perform the audit trail search and initial analysis, attend court approximately eight to ten times per year.
The Queensland Evidence Act 1977, Section 95 'Admissibility of statements produced by computers' is relied upon for court appearances. If the Audit Trail is required in Court, the Security Officer in accordance with Section 95, prepares a statement and obtains a Certificate. The Certificate requires the person occupying a responsible position to provide a statement that the computer systems were 'operating properly'. Since the move from a closed mainframe environment the information systems branch management are becoming more reluctant to sign these certificates. The larger and more diverse the systems become the more difficult it is to have one person only vouch for secure operations. An even greater concern is the challenge of giving evidence in court if the certificate is challenged (Queensland Evidence Act, 1977).
Over the last 12 years, in the state of Queensland Australia, 100 information system audit trails have been required for the furtherance of legal proceedings. Of these 100 cases, 11 have been chosen for analysis and review to provide an initial assessment against a preliminary set of 13 major themes in relationship to the secure maintenance of audit trail facilities and presentation of related evidentiary materials. These themes will be further revised and assessed in the second paper produced from this project which will further analyse the results and place them into current context in relationship to emerging and accepted information systems security management practices. The cases are listed in Table 2. One case is a civil matter the other cases relate to criminal matters. The cases have been evaluated against the 13 major themes or criteria as listed in Table 1.
|
Criteria |
Criteria |
||
|
1 |
Proof of user activity |
2 |
Technical security for Audit Trails |
|
3 |
Expertise of Information Technology Staff |
4 |
Relevance of Section 95 Certificate |
|
5 |
Proof of a business process |
6 |
Audit Trail Content |
|
7 |
Rules of Evidence |
8 |
Recording of details by Police Officers |
|
9 |
Time and relevance of routine checks |
10 |
The recording of all activity |
|
11 |
Functionality of application systems |
12 |
Positive identification of a user |
|
13 |
Documentation for pertinent information technology process and procedure |
Table 1: Criteria for Significance of Evidence
|
Type of Request |
Case |
Audit Trail Use |
Year |
Offence |
Outcome |
Section 95 Certificate Tendered |
|
|
Operational |
|||||||
|
1 |
R v Atwell |
Investigation |
2000 |
Rape |
Guilty Verdict |
Not Required |
|
|
2 |
R v Dawson & Tanner |
Hearsay |
1996 |
Armed Robbery |
Guilty Verdict |
Yes |
|
|
3 |
R v Grimley |
Investigation |
2000 |
Assault causing grievous bodily harm |
Guilty Verdict |
Yes |
|
|
4 |
R v McClymont |
Evidence |
1996 |
Disqualified Driving & Stating a False Name |
Guilty Plea |
Yes |
|
|
5 |
R v Scriven & Cook |
Evidence |
1993 |
Attempted Murder |
Guilty Verdict |
Yes |
|
|
6 |
R v Vaughan |
Evidence |
2000 |
Assault with Intent to Rape |
Guilty Plea |
Yes |
|
|
Misuse |
|||||||
|
7 |
R v Hogan |
Evidence |
1998 |
Misappropriati on of Property |
Guilty Verdict |
Yes |
|
|
8 |
R v Luther |
Evidence |
1988 |
Stealing |
Guilty Verdict |
No |
|
|
9 |
R v Swift |
Evidence |
1998 |
Official Corruption & Perjury |
Guilty Verdict |
Yes |
|
|
10 |
R v Spidalieri |
Evidence |
1999 |
Official Corruption & Perjury |
Guilty |
Yes |
|
|
Civil Matter |
|||||||
|
11 |
Jaques v Queensland Police Service |
Evidence |
1997 |
Sexual Harassment |
Applicant Withdrew |
Yes |
Table 2: Case Summary
Case Summary: The accused was charged with rape, attempted rape, burglary, indecent assault, burglary with violence and disable to commit an indictable offence. There were about 30 charges in all. The offences were all committed during a comparatively short period between the end of 1997 and the beginning of 1998. The 11 victims were all older or elderly women ranging in age from 59 to 86 years. All lived alone in home units or flats in the southern suburbs of the city of Brisbane. The offences took place at night or in the early hours of the morning. This offender was dubbed the 'Granny Rapist' by the police and the media.
Police involved in the investigation had the description of a vehicle believed to belong to the offender. A police officer, who had previously been called to investigate a reported disturbance 12 months earlier, remembered that he had made a computer check on a vehicle matching the description of the offenders vehicle.
Audit Trail Analysis revealed that a computer check for a vehicle matching the description was made at the time stated by the officer and details of the registration number and the registered owner of the vehicle were displayed. Investigating police interviewed the owner and took a saliva sample that matched DNA samples obtained from the various crime scenes.
Audit Trail in Evidence: No statement or certificate was required as the audit trail searches were used in the investigation process only and not required in evidence.
Outcome: The accused was found guilty and sentenced to life imprisonment. In July 2000 the Court of Appeal refused an application for appeal.
Commentary: The audit trail played a significant role in assisting the investigation. Given the 'Modis Operandi' of the offender, it is not unrealistic to believe that another or several other elderly females may have become victims had the audit trail not been available.
Significance: This case has highlighted significant factors 5 and 9, where a routine check initially not important enough to record in the police officers notebook at the time but later became an essential piece of intelligence information in the investigation of a very serious criminal offence. It also emphasises the need for the generation and retention of audit trails for proof of business process for extended periods.
3.2 Case 2: R. v. Dawson & Tanner
Case Summary: The Committal hearing was held over three separate periods in 1995. The two persons accused were charged with 'armed robbery in company' and 'unlawful use of a motor vehicle'. The trial was held in the Brisbane District Court in April 1996. The case for the Crown was that the two accused entered a video store with their faces and heads covered and robbed the two assistants, one male and one female, at gun point. The accused then left the store and drove away in a car. The car, which had been stolen from a shopping centre car park, was later found in close proximity to the video store with the door open and the motor still running. A latent fingerprint was found in the vehicle that matched one of the accused.
A male eyewitness saw the accused run from the store and took note of the registration number and description of the car. He then went inside the store and gave the details to the male and female assistants. The male took note of the details. The female assistant called the Police Communications Centre and provided the police officer who answered, with details of the incident which included the information given by the eyewitness.
When the case came to trial the eyewitness could not remember the details of the vehicle and the store assistants no longer had a written record of it and could not remember the details. Police officers who attended the incident failed to write the number of the 'get away' vehicle in their notebooks but they telephoned the information through to the Crime Reporting Data Entry Centre from the video store in accordance with policy and procedure.
Audit Trail Analysis verified the registration number of the vehicle had been given to the Officer at the Police Communications Centre and had been entered at the time of the original CRISP entry. Two queries were also made on the vehicle on the afternoon in question by officers at the Police Communications Centre.
Audit Trail in Evidence: The prosecution tried to submit the original computer entry on CRISP as being 'notes made at the time'. The audit trail evidence was ruled 'hearsay' and not admitted. This was due to the action of the Judge ruling all evidence in respect of the registration number of the car being inadmissible due to hearsay. The registration number was evidence proposed to be adduced from the female store assistant. Given that this was ruled hearsay, all computer records in relation to the female store assistant's evidence were inadmissible.
Outcome: The prosecution dropped the armed robbery charges and the defendants pleaded guilty to some property related charges. They were sentenced to 18 months imprisonment.
Commentary: This case could be described as a 'comedy of errors'. Given that the process of law must be followed, it is worth noting the effect of the human factor in this case. No normal citizen is taught about 'process and procedure' or how to respond and what to record when being threatened by a firearm. Victims of crime can be forgiven for not recording details to a level acceptable in a court of law, but the police cannot. The officers were remiss in not recording the vehicle details in their notebooks. The evidence was ruled hearsay because the information had passed through many hands and no-one had recorded the registration number.
This case was serious, the punishment did not fit the crime and the audit trail information could not be used to verify and confirm the process. The offence would have attracted a harsher and more appropriate penalty, had correct process and procedure of recording the incident been followed.
Significance: This case has highlighted the significance of factors 7 and 8. The non recording of information at the scene of a crime, pertinent to a case, cannot be substituted in a legal sense by the audit trail even if the information is recorded in that audit trail. It has been shown that audit trail information is not accepted when hearsay is involved through inappropriate process.
Case Summary: The trial was held in the Stanthorpe District Court in 2000. The accused was charged with assault causing grievous bodily harm. The case for the Crown alleged that the accused struck the complainant on the face and broke his jaw in two places. The defence counsel alleged that fabrication or 'doctoring' by the police of records of evidence, namely the 'Crime Report' and the 'daily occurrence sheet' had taken place. The crime report was recorded on computer at the time of the incident. The defence alleged that the report was later changed and what was being presented was not in fact what was initially recorded.
Audit trail analysis located details of the original recording of the Crime Report made by the police officers at the time of the incident. Analysis also showed that information had only been added to the report, in keeping with normal process and practise, and that no modifications to information had taken place.
Audit Trail in Evidence: A statement produced by the information security officer, who performed the audit trail searches and a statement produced by the CRISP data entry operator who entered the original crime report were accepted by the defence. Neither was required to give evidence. A certificate under S.95 of the Evidence Act was tendered. There was no recorded challenge to the audit trail information.
Outcome: The accused was found guilty and sentenced to two and a half years imprisonment.
Commentary: Information recorded on a computer can be modified or deleted without leaving an obvious trace in a file or database if the system does not provide for a history of record changes, i.e. each time a piece of information changes a separate record is written to a database. Under forensic examination of a computer disk on which the data are stored it may be possible to retrieve some of the original information, depending on how much over-writing to that particular disk area has taken place. In this case forensic examination would have been a last resort as the system resides on a mainframe where disk writing is extensive and examination of the disk would have caused considerable delay to operational processes. The only other way of determining what has taken place is to have an audit trail to record activity at the actual application level. The CRISP computer application system does not provide for a history of each CRISP report change.
The audit trail was accepted without challenge. The statements were accepted by the court without testimony by the security officer or the data entry officer. There was no technical challenge to the audit trail and no mention of verification of audit information. Even given the allegation of system interference, there was no challenge once the audit trail was produced.
Significance: This case has highlighted significant factors 2, 5, and 6. Firstly there was no challenge to the audit trail and testimony was not required. Secondly, there was a requirement to confirm and provide proof of a business process and thirdly it would appear the defence counsel did not know how or did not believe it worthwhile to challenge from a technical perspective.
Case Summary: This hearing was held at the Redcliffe Magistrates Court, in the Brisbane area Queensland, in April 1996. The accused was charged with disqualified driving and stating a false name. He pleaded guilty to the disqualified driving charge but contested the false name charge.
Audit Trail Analysis verified that computer checks were made on the defendant with names different to his actual name, as later obtained.
Audit Trails in Evidence: The defendant was shown the computer print outs and he then pleaded guilty to the false name charge. There was no challenge to the audit trail evidence.
Commentary: In this case it was the accused that accepted the audit trail information without question.
Significance: This case has highlighted significant factor 2. Audit trail data, well developed and presented, may be accepted in court without challenge. This can be a significant factor in court proceedings.
3.5 Case 5: R. v. Scriven & Cook
Case Summary: The Committal hearing was held in the Rockhampton Magistrates Court, Queensland, in 1993. The accused were charged with Attempted Murder, Grievous Bodily Harm and Wounding. Three trials were attempted or held at the Supreme Court Rockhampton between 1993 and 1994. The first two trials were deemed mistrials. The case involved a taxi driver who responded to a 'fare' involving two males. One of the males got into the front seat and one in the back. After a brief conversation the male in the back seat slashed the throat of the driver whilst the male in the front gouged his eyes and stole his nightly takings. The two then ran to a motor vehicle and the taxi driver gave chase. They changed vehicles a few streets away and the taxi driver radioed through a description of the get-away vehicle and then drove himself to the hospital. A police officer on duty that evening made routine computer checks via police radio on vehicles he sighted answering the description given by the taxi driver. One of the vehicles checked was registered to one of the accused.
Audit trail analysis verified that the computer check for that vehicle was made at the time stated by the officer. The 'user-id' used to make the check was assigned to the officer who was the computer operator on the evening in question. This placed the vehicle in a certain location at a given period of time and corroborated other evidence given. The accused was identified as a person seen drinking in a hotel nearby.
Audit Trail in Evidence: A statement was submitted by the security officer responsible for the audit trail searches. Evidence was given at the first trial and then accepted at the other two trials without further question. There was no attempt to challenge the audit trail evidence.
Outcome: Both of the accused were found guilty and sentenced to 8 years imprisonment with no recommendation for early parole.
Commentary: Where no mobile computer facility is available it is standard police practice for officers to use the radio, from their vehicle, to contact the nearest Police Communications Centre or command centre and verbally request a computer check to be performed on their behalf. Policy and procedure for this exists in (Queensland Police Service, 2001). Many of the checks are routine and not always recorded in the Police officer's notebook. This standard business process was followed by the officer in this case and no record was entered into his note book. The non recording by the officer was not challenged. The officer stated he radioed for a check, the operator on duty confirmed the call and the computer check, and the audit trail verified and confirmed both officers' statements. There was no challenge to the audit trail information from a technical perspective.
Significance: This case has highlighted significant factors 2, 5, and 8. Firstly, the need for proof of business process and secondly the audit trail evidence was accepted without challenge and thirdly there was no requirement for a record in the police officers notebook.
Case Summary: The accused was charged with 'assault with intent to rape' and 'abduction with intent to carnally know'. The trial was held in the Brisbane District Court in May 2000. Documents relating to the investigation had been inadvertently destroyed and all computer system activity needed to be reconstructed.
Audit trail analysis verified computer checks made by the 'intelligence officer' involved in the investigation. It showed that numerous checks had been performed which built a profile of the accused. This profile was used as the basis for a warrant that resulted in the arrest of the accused.
Audit Trails in Evidence: A statement was produced by the security officer who performed the audit trail searches and a certificate under s 95 of the Evidence Act 1977 was tendered. The statement and certificate were not needed at the trial as the defendant pleaded guilty.
Outcome: The verdict was 'guilty' and the accused was sentenced to 6 years imprisonment.
Commentary: It is standard practice for intelligence officers to print results of computer searches. If all activity performed on the information systems had not been recorded in an audit trail the reconstruction would not have been possible.
Significance: Factors 6 and 10 are the two significant issues highlighted in this case. Firstly, the audit trail was used as a backup for misplaced/destroyed printed documents and secondly the importance of recording of all activity to provide complete reconstruction of all events was highlighted.
Case Summary: The Committal hearing was held in 1996. The accused was a Queensland Police Officer charged with the offence of 'Misappropriation of Property with a Circumstance of Aggravation'. Two trials were held in the Brisbane District Court. The first trial in February 1997 resulted in a 'hung' jury. The second trial was heard in February 1998. The case for the Crown was that the accused was in-charge of a police raid on a brothel in 1992. Money was seized and that money ought to have been dealt with following normal procedure for the handling of seized property. It should have been handed in at the property section at police headquarters with certain records kept including data entry into the computer and a hand written record in the property book with a receipt issued. Given the raid was completed after hours the procedure is for all property to be handed to the police officer working at the front desk in the foyer at police headquarters. The accused claimed he did hand the money in at the front counter although he could not produce a receipt. The property officer claimed he had not received the money from the accused.
Audit trail analysis revealed that the only additions and changes made to the system were as follows:
-
The senior constable on duty at the front counter at police headquarters was the only person to use the front counter computer terminal on the night in question;
-
Between January and April 1992 there was only one instance where the 'Exhibit System' was queried by the property officer to display all exhibits deposited by the accused;
-
No queries were performed on the Exhibit System by the accused between January and April 1992;
-
Twenty one additions were added to the exhibit system on the date of the raid on the brothel and for two days after that date. Screen prints of these were obtained from the database as they appeared in 1995 and compared with screen prints from the audit trail as they were entered in 1992. 3 of these 21 records were entered by a person with a user-id assigned to the Senior Constable on duty the night in question. A comparison showed that no change had been made.
-
All queries performed on the audit trail showed that none of the exhibit entries on the day in question related to a large amount of money.
The Audit Trail in Evidence: Under cross-examination at the committal hearing there was a challenge to the application system (exhibit system) in relation to errors in the computer where it failed to record or failed to send information. It was stated in response that the audit records would show the screen with an appropriate error message had the exhibit entry transaction failed. This would occur for all errors regardless of the number of times attempted.
At the second trial there were questions under cross-examination about the functioning of the computer applications. Also questions were raised about procedures at the property office. These questions were unrelated to the audit trail and security of the systems and not the responsibility of the security officer to answer.
Outcome: The accused was found guilty and sentenced to two years imprisonment.
Commentary: This case is different as it was requesting proof that an activity did not happen which is the reverse of most other requests. Without full recording of every activity performed by users it would have been impossible to show with confidence that the exhibit had not been entered. Recording partial activity without full screen audit would not have produced conclusive results.
Significance: This case has highlighted significant factors 10, 11 and 2. Firstly, there is need to retain all activity performed on data which includes a full screen audit. Secondly, a challenge to the security and functioning of an application system is quite possible, and thirdly there was no technical challenge to the audit trail process itself.
Case Summary: The trial was held in the Brisbane District Court in December 1988. The accused was a Queensland Police Officer charged with stealing a motor vehicle, forgery and misappropriation. The case for the Crown alleged that the accused was part of an organised car-theft-racket responsible for the theft of good quality motor vehicles, the changing of their appearance and registration details and then their sale with sharing of the profits. The accused had met a known criminal at a function and this person allegedly became one of his accomplices. The QPS computer systems were used by the accused to obtain vehicle details.
Audit trail analysis revealed that:
-
Whilst working 'evening shift' a computer check was performed by the accused which showed the last 16 motor vehicles stolen in Queensland (also known as the 'hot list'). This check was apparently done to obtain information as to when particular types of vehicles were reported stolen;
-
A vehicle registration check for a particular vehicle was performed and the engine number obtained. Engine numbers were then queried until an almost identical number was found. The engine number on that particular vehicle was changed by replacing a '4' with a '1';
-
The next day the accused registered a particular vehicle with the changed engine number;
-
The audit trail information verified the evidence given by the accused's accomplice who had stolen the vehicle. The car belonged to a relative of the accused. The accused knew the location and the theft was premeditated and organised;
-
Further audit searches showed that the accused made a criminal history computer check on his accomplice the night after he met him.
Audit Trail in Evidence: Statements were tendered by two information security officers and the computer systems officer who performed the audit trail checks. A certificate under s.95 of the Evidence Act was suggested but the prosecutor said he had not heard of it and decided not to worry about it.
Three QPS people were questioned in relation to the audit trail evidence. One, the security officer was questioned under cross-examination in relation to the use of 'user-ids and passwords'. Questions concentrated on the following themes:
-
the ability of any person to see what password is keyed into the computer by a user;
-
the determination of responsibility for changing passwords;
-
the procedure to be followed if another person modifies the password;
-
access by the security administrator to the password in an unencrypted form; and
-
the number of times people 'play tricks' on each other by modifying passwords.
The second person, a senior security officer, was also questioned about persons playing 'practical jokes' by modifying another persons' password.
Under cross examination the third person, the computer systems officer, was questioned by the defence and the questions asked had an expectation of 'expert' in the knowledge and operation of the application system. The witness was unable to answer many of the questions posed. There was no attempt to challenge technical aspects of the audit trail.
Outcome: The accused was found guilty and sentenced to six years for misappropriation, five years for stealing a vehicle, and two years for forgery, to be served concurrently with parole possible after two years.
Commentary: Evidence from the audit trail was crucial in this case. Indeed, without the audit trail, it is doubtful that there would have been a case at all. The defence challenged the functioning of the application system and user access control, in particular the possibility of users playing practical jokes by using another persons 'user-id'. The third witness, the computer systems officer, was responsible for technical support of the computer on which the application systems run and on which the associated audit trails are stored. He was not responsible for application development. Unbeknown to the defence, and possibly the prosecution, this witness was also the person responsible for the support of the audit trail sub system. An ideal opportunity for a challenge to the technical configuration of the audit trail system was missed due to lack of knowledge of information technology issues by legal counsel.
Significance: This case has highlighted significant factors 2, 3, 12, 13. Firstly, there was no challenge to the technical security of the audit trail itself. Secondly there is need for IT expertise to be developed for evidentiary purpose by legal counsel. Thirdly, the ability to positively and unreservedly identify a user electronically is not possible by using 'user-id and password' combinations only and, fourthly, pertinent IT processes need to be documented.
Case Summary: The accused was charged with official corruption and three (3) counts of perjury. The trial was held in the Brisbane District Court in July 1998. The case for the Crown alleged that the accused agreed to receive a benefit of $3,000 on account of his later checking computer records with a view to the protection of an intended offender from detection. The accused would inform the intended offender of any police interest in, or investigation of, him in respect of suspected criminal activity. The intended offender (who was a covert agent working for the Criminal Justice Commission) knew of a drug dealer on the Gold Coast who had previously claimed to him that she enjoyed corrupt police protection. He pretended to the drug dealer that he was involved in a drug operation and wanted similar protection from police. The dealer put him in contact with a third person who brought in a former police officer who was a friend of the accused.
Audit Trail Analysis revealed that over a twelve month period a number of computer checks were either attempted or made, across a number of computer systems, by the accused involving the name of the covert operative, from a terminal assigned to the location where the accused was stationed.
Audit Trail in Evidence: The prosecution questioned in general the confidentiality of information and access control to authorised users including the login banner and terminal and user access. The defence under cross-examination re-visited the checks made by the accused but at no stage questioned the technical validity of the audit trail.
Outcome: The accused was found guilty and sentenced to five and a half years imprisonment.
Commentary: Swift was not a competent user of the computer systems. The process used for actions performed were indicative of this fact. Whilst access control and authorisation of users were mentioned by the prosecution, the defence did not attempt in all seriousness to challenge the accuracy and validity of the audit trail records.
Significance: This case has highlighted the significance of factors 2, 12. Firstly there was no technical challenge to the audit trail process itself. Secondly, a challenge is possible to the identification of a user and the security of transactions performed by that user.
3.10 Case 10: R. v. Spidalieri
Case Summary: The accused was charged with six counts of official corruption and two counts of perjury. The trial was held in the Brisbane District Court in May 1999. The case for the Crown alleged that the accused, a former police officer, was involved in activities of arranging meetings between, and requesting money from, known criminals with the intent of paying corrupt serving police officers. See 3.9 in the prior case of R v Swift.
Audit trail analysis revealed that computer checks made by Swift, a serving police officer, had been performed.
Audit Trail in Evidence: Under examination-in-chief the witness was questioned about the construction of user-ids and the use of user-ids and passwords in particular the number of days for which a password is initially activated before a user changes it. Under cross-examination there was a challenge to:
-
the printing of material, the location of printers and the ability of others to see the information printed;
-
the amount of security training for police officers;
-
whether or not checks performed were normal police procedure for registering an informant, and;
-
the level and position held within the information security section by the witness
Under re-examination the prosecution confirmed with the witness the information security training provided to police. No challenge in a technical sense was made.
Questions were asked in relation to the analysis of the audit trail information. Full analysis is not the responsibility of the system Security Officers. The majority of analysis is completed by the investigating officer or intelligence analysts.
Outcome: The accused was found guilty and sentenced to six years imprisonment on the corruption charges and two(2) years for each perjury charge; to be served concurrently.
Commentary: Examination of evidence and challenge to certain aspects was limited but the most comprehensive of the cases reviewed. However, there was no technical challenge to the audit trail process itself.
Significance: This case has highlighted the significance of factors 3, 8, 12, and 13. Firstly, a challenge to the expertise of information technology staff is possible. Secondly, a challenge is possible to process and procedure which includes recording of information on computer systems. Thirdly, a challenge is possible to the identification of a user and the security of transactions performed by that user. The fourth significant factor showed there was no technical challenge to the audit trail process itself.
3.11 Case 11: Jaques v. Queensland Police Service
A complaint was made in 1993 by a Constable of police in relation to sexual harassment involving Jaques. He was dismissed from the Queensland Police Service as a result of the investigation of the complaint. In 1997 he made application to the Queensland Industrial Relations Commission for reinstatement to the Queensland Police Service on grounds of unfair dismissal.
The constable claimed the harassment took place via a telephone call to her residence. The applicant denied making the telephone call. Queensland Police Service telephone records were checked to verify the time and date of the call and the location of the telephone extension.
Audit trail analysis revealed that the computer system had been used by the applicant at the time the telephone call was made. Further analysis revealed a pattern of misuse by the applicant over a fourteen(14) month period where he had queried his neighbours, friends, relatives and persons who had previously made complaints against him. He had also performed checks on current and previous senior members of the service including members who had died in the line of duty.
Audit Trails in Evidence: A statement was produced by the security officer who performed the audit trail searches and the system was demonstrated to the hearing via secure "dial up" data line connection. The corroboration of computer use and time of the telephone call was introduced as circumstantial evidence. The security officer gave evidence for the Queensland Police Service but was not cross examined due to the discontinuance of the case. Audit trail evidence was accepted by both parties involved in the action.
Outcome: The applicant withdrew his application for re-instatement.
Commentary: The audit trail evidence was corroborated by telephone logs, thus, providing an alibi from both the computer and telephony systems. The application was withdrawn with no attempt to challenge either of the audit trail processes.
Significance: This case has highlighted the significance of factor 2 which shows there was no technical challenge to the audit trail process itself.
Legal and court proceedings do not yet appear to be at a level to fully assess the worth and acceptance of electronic evidence. This is demonstrated by the low level of cross-examination and the acceptance of material as submitted at face value. The cases considered in this paper pre-date the digitisation of the court itself which may in the future contribute to more in-depth consideration at trial time.
A study of the cases involving evidence given by QPS information security officers has shown that none of the evidence presented has ever been rejected or seriously challenged from a technical perspective. The information system audit trail records are readily accepted by both prosecution and defence. It has been shown that audit trail records are seldom if ever challenged however these same records may be critical to the prosecution of a case.
The lack of competence of the legal profession for both prosecution and defence in the presentation and challenge of electronic evidence relating to audit trails is strongly evident. This has been observed from the court room and through the investigation processes. This is also possibly why QPS evidence in relation to audit trails has never been rejected or strongly contested and challenged.
This factor was also demonstrated in the questioning of witnesses relating to activities and responsibilities outside their control. Questions were asked of the security officers that operational police should answer. In addition, questions were also asked that investigating police should answer in relation to in-depth analysis of audit trail information.
The provision of an Alibi has been shown for several cases where the audit trail checks were able to place a police offer at a particular location when the check was being performed and possibly an unwanted alibi for the accused when it was shown that he was in a place he claimed not to be. Also, the lack of an ability to positively identify a user electronically has been identified in several cases. This may in the future become extremely important to proving who was responsible for a legal or financial transaction.
Given future trends, where legal professionals are cross trained in information technology, it is probable that in-depth analysis in court may take place. The adoption and move away from mainframe to commodity based systems could give rise to ability to challenge systems in use by law enforcement agencies. Mainframe systems provided a higher level of security, hence the current move is showing that there is no longer a distinction between a police system and other commercial systems.
Acknowledgements
This paper has been edited and reviewed by Professor William Caelli, Head of School of Data Communications, Queensland University of Technology(QUT), Brisbane, Australia.
Allinson, C L (2001), 'Information systems Audit trails in Legal Proceedings as Evidence', Computers & Security, Vol 20 Number 5, England, Elsevier Advanced Technology.
Carter, W J (1997), Police and Drugs: A Report of an Investigation of Cases Involving Queensland Police Officers, Brisbane, Criminal Justice Commission.
CJC (2000), Protecting Confidential Information, Brisbane, Criminal Justice Commission.
Fitzgerald, G E (1989), Report of a Commission of Inquiry Pursuant to Orders in Council, Australia, The Government Printer Queensland.
ISO/IEC 15408-1 (1999), Information Technology ? Security Techniques ? Evaluation Criteria for IT Security ? Part 1: Introduction and General Model, USA.
NCSC (1987), A Guide to Understanding Audit in Trusted Systems, USA, National Computer Security Center.
NSW Ombudsman (1995), Confidential Information and Police, NSW, Office of the Ombudsman.
Parker, T and Sundt, C (1993), Information Security Handbook, England, International Computers Limited.
Queensland Evidence Act 1977, s.95.
Queensland Police Service (1992 ? 2001) Operational Procedures Manual, Australia, Queensland Police Service.
Wood, J RT (1997), Royal Commission into the New South Wales Police Service, Final Report Volume II: Reform, Sydney: Independent Commission Against Corruption.