Cyber-Physical Systems Security
1. PowerSPRINT: Power Grid IoT System Protection and Resilience using Intelligent Edge
Funding Body: EPSRC-PETRAS National Centre of Excellence for Cybersecurity of IoT Systems, UK, Oct. 2021 – June 2023
PI: Dr Subhash Lakshminarayana
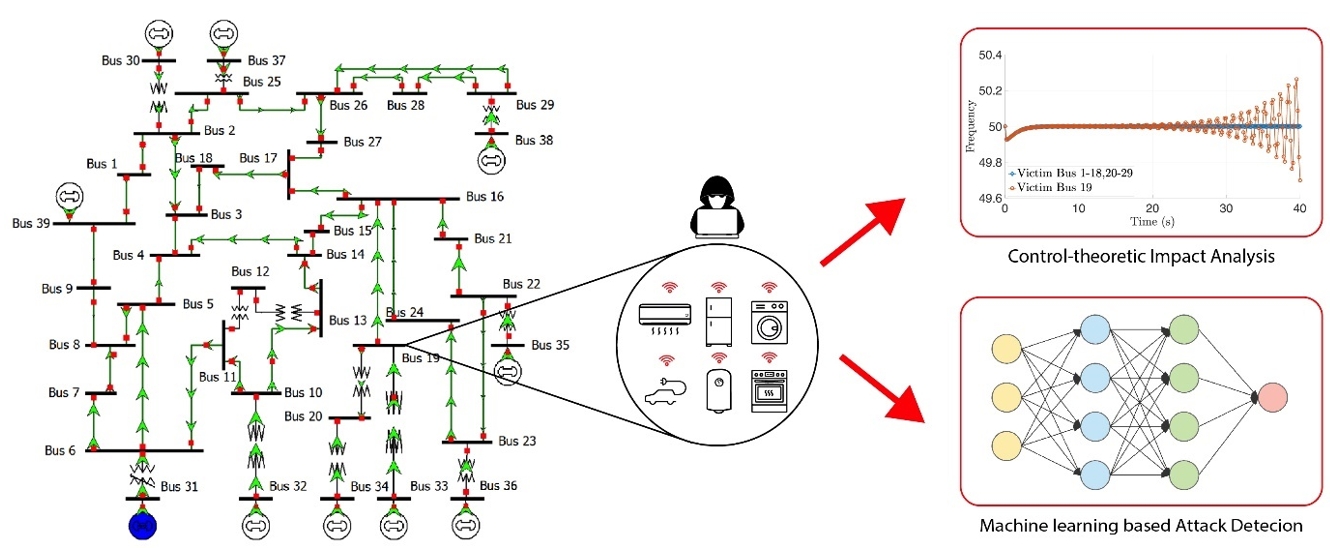
The Power-SPRINT project investigated the cybersecurity risks posed by the growing integration of IoT-enabled smart-home appliances on power grid operations (e.g., smart electric vehicle charging stations, heat pumps, etc.). The vulnerabilities in these devices can be used to launch large-scale load-altering attacks (LAAs) that can disrupt the grid's power balance. These threats are nationally significant for the UK (and worldwide) as evidenced by the recent consultation launched by the UK's Department of Energy Security and Net Zero (DESNZ). The project provided a comprehensive framework for LAAs. It included three streams:
- Threat and risk likelihood analysis: By analysis of network attack data from IoT-home appliances, we performed identification of the devices that are most likely to be targetted by the attacker as well as the level of protection offered by different security enhancements.
- Attack Impact Analysis: By studying power grid control loops (e.g., frequency/voltage control) under IoT-enabled load altering attacks, we identified the locations of the least effort attacks. We also determined the locations in the power grid that require security enhancement to prevent destabilizing attacks.
- Development of an intrusion detection system: To detect IoT-enabled load altering attacks, we performed real-time analysis of the power grid's physical signals monitored using smart meters (e.g., load consumption, voltage, frequency, etc.). We developed a machine-learning model that can effectively analyse and learn from data using privacy-protected data, with protection implemented at edge nodes.
2. CLADDED: A Cross-LAyered Data-Driven System for Electric Vehicle Charging Stations Attack Detection
Funding Body: Innovate-UK CyberASAP program, Apr. 2022 – Feb. 2023
PI: Dr Subhash Lakshminarayana
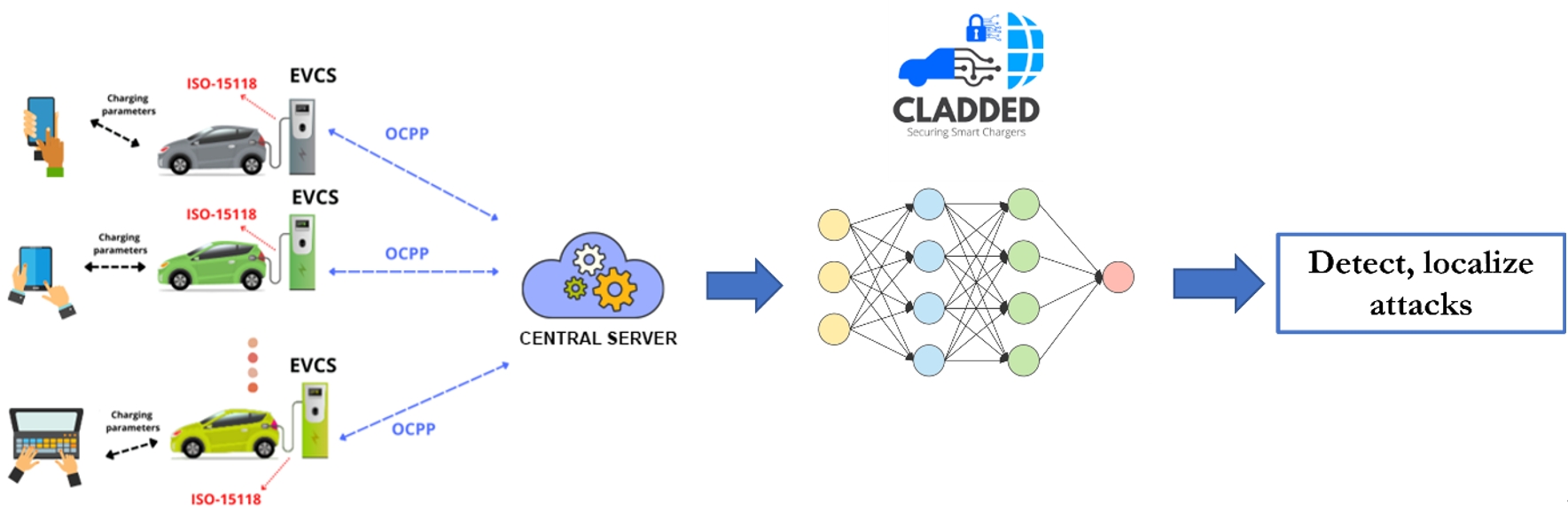
The UK government's ambitious net-zero goal will result in the fast acceptance of electric vehicles (EVs) and the implementation of EV charging stations (EVCS). Global legislation, such as the AEV Act (UK) and National Electric Vehicle Infrastructure Formula Program (NEVIFP, US), will lead to a significant uptake of “smart" electric vehicle charging stations (EVCS) that can send/receive data from users and provide real-time response to their charging preferences. However, the connectivity features of smart EVCS raise cyber security risks that could have severe consequences for power grid operations as they may serve as entry gates for adversaries to penetrate the power grid and disrupt its operation by manipulating demand. Additionally, attacks can result in denial-of-charging, which can have a grave social impact (e.g., people unable to reach their offices or hospitals). These IoT-enabled high-wattage charging points are widespread across the UK (around 400,000 private and 42,000 public charging points), so it could be difficult to identify hostile variations from routine power demand fluctuations due to EV charging. Moreover, the lack of security standards in this industry means that these charge points can be vulnerable to cyber attacks. Thus, security solutions are very important.
CLADDED offers cutting-edge artificial intelligence (AI)-based solutions for EV charging firms that seek to secure their charging points. Specifically, CLADDED monitors the charging profiles of various EVCS in real-time carefully learns the charging patterns through advanced AI-based algorithms, and alerts the system administrator of any suspicious activity (malicious charge/discharge). CLADDED updates itself automatically, adapts to changing user charging patterns, and carefully differentiate between natural demand variations and cyber attacks.
3. Local Energy Markets for Distributed Energy Resources Management using Resilient and Private Reinforcement Learning Control
Funding Body: King Abdullah University of Science and Technology Opportunity Fund Program, Jan. 2024 – June 2025
PI: Dr Subhash Lakshminarayana
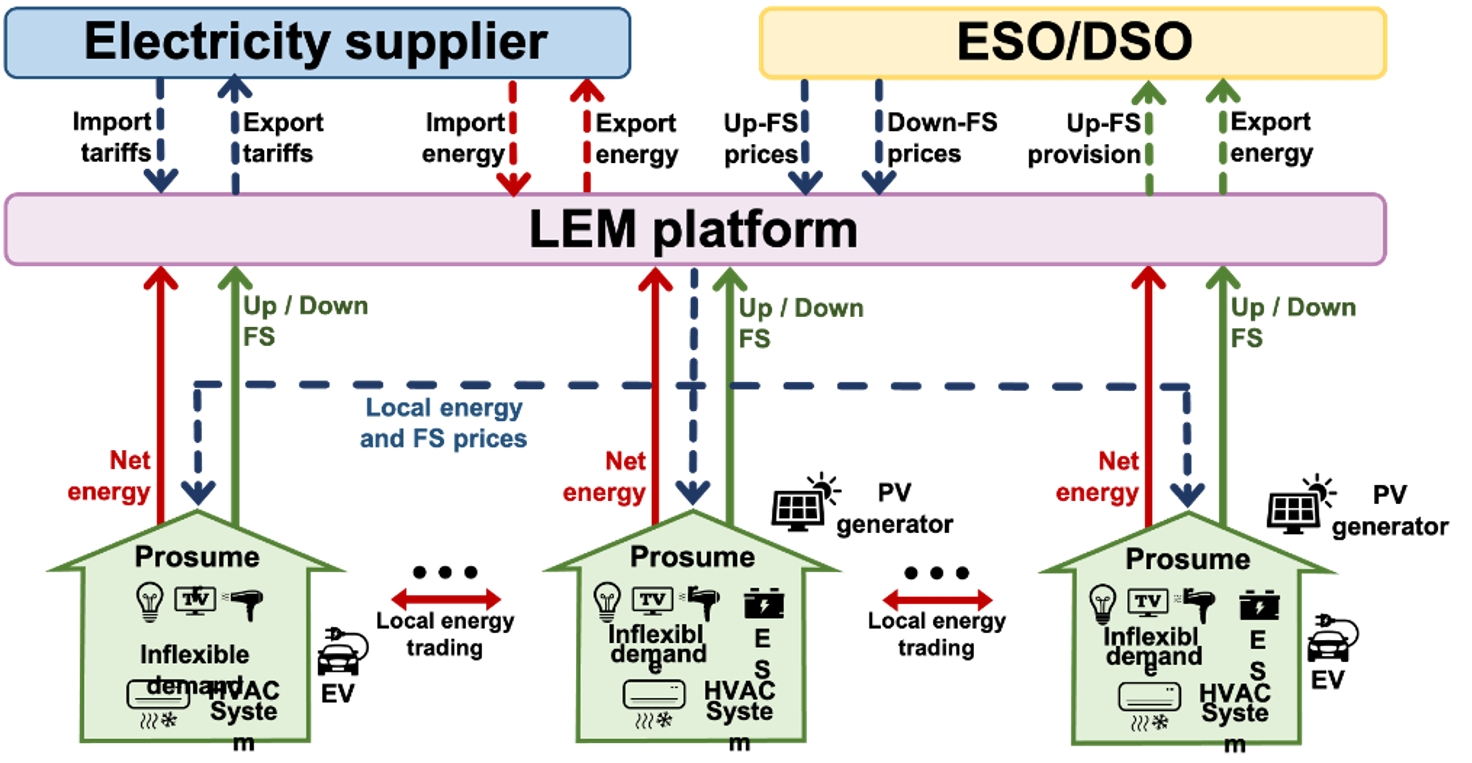
Peer-to-peer (P2P) energy trading and flexibility services (FS) provision in local electricity markets (LEMs) are becoming increasingly important due to a range of factors, including the need to ensure grid stability and efficiency, the problem of costly infrastructure upgrades, and the promotion of sustainability, energy security, and community participation in energy decision-making processes. These markets enable the efficient use of local energy resources, reduce the reliance on centralized generation and transmission, and support the transition to a low-carbon energy system. This project aims to explore the use of LEMs to manage distributed energy resources (DERs) through coordinated P2P energy trading and FS provision in a model-free decision-making approach using multi-agent deep reinforcement learning (MADRL).
Although data-driven control methods are already supporting the integration of DERs into the grid, there are also security and privacy issues that impede their deployment in practical systems. LEMs can be attractive targets for malicious agents aiming to make financial profits. The adversaries can be malicious insiders participating in the LEMs or external entities manipulating the data exchanged between the participating agents. The attacker can influence the RL decisions by injecting elaborate perturbations into observations, which could further destroy the RL-based system operation. On the other hand, RL-based agents do potentially leak privacy-sensitive information from the trained policies. Thus, to deploy MARL algorithms in LEMs, there is an urgent need to enhance the resilience against adversarial attacks and the ability of privacy-preserving for the training data. This project with the proposed learning method encapsulates the economic benefits of both local energy trading and FS provision functions, while ensuring the designed algorithms do not leak private information during their training process and are resilient against variants of cyber-attacks.
